Smart Security
Network Security
WatchGuard Triple Threat in Info-Tech NGFW Vendor Landscape Report
In an increasingly complex network threat landscape, delivering security solutions that stop malware in its tracks requires more sophisticated technologies than ever. Traditional firewalls aren’t enough and only stop a portion of signature-based threats. Today’s unknown threats require Next-Generation Firewall (NGFW) solutions that provide complete network security and real-time threat visibility.
When Info-Tech Research recently evaluated the top ten NGFW vendors for its 2014 NGFW Vendor Landscape Report, WatchGuard was more than just a “Champion,” they were also the only vendor given the Value and Trend Setter Awards. Info-Tech noted WatchGuard is only the second vendor to place first in all three evaluation categories in any of the 70+ landscape reports they publish annually.
 WatchGuard’s Fireware XTM Series NGFW was the most highly rated among all vendors and was one of only two vendors to receive the highest designation in the report’s Overall Product category. They found the XTM series “provided an affordable price with a solid and scalable product.” Info-Tech was also impressed by the reporting capabilities of the XTM firewall and called WatchGuard Dimension a “differentiator amongst its competitors.”
WatchGuard’s Fireware XTM Series NGFW was the most highly rated among all vendors and was one of only two vendors to receive the highest designation in the report’s Overall Product category. They found the XTM series “provided an affordable price with a solid and scalable product.” Info-Tech was also impressed by the reporting capabilities of the XTM firewall and called WatchGuard Dimension a “differentiator amongst its competitors.”
The combination of WatchGuard’s innovations like WatchGuard Dimension and its promise to always deliver affordable security solutions for organizations of all sizes, continues to separate them from other vendors.
For this Vendor Landscape, Info-Tech chose the ten vendors with broad capabilities across multiple platforms with a strong market or reputational presence among mid- and large-sized enterprises.
Download the Info-Tech report today: www.WatchGuard.com/InfoTech
WatchGuard Technologies a Leader in Three Key Unified Threat Management and Next-Generation Firewall Categories in Frost and Sullivan Report
Companies of all sizes are demanding increased functionality from their network security and management solutions that won’t compromise performance. As the threat landscape shifts from known, signature-based threats to zero-day, advanced malware threats, detecting and eradicating them requires a multi-layered approach to security and real-time threat visibility. Delivering the industry’s best-of-breed security with industry-leading performance requires a commitment to product development and continual assessment of how to improve.
Today, WatchGuard was recognized for its commitment to product development and identified as a leader in three categories of Frost & Sullivan’s 2014 Global Analysis of UTM (Unified Threat Management) and NGFW (Next Generation Firewall) Market research study. In the report, WatchGuard outperformed other vendors in Management and Usability, Flexibility, and Value. WatchGuard was also noted in the areas of Performance and Scalability, and Roadmap.
Chris Rodriguez, senior industry analyst for network security at Frost & Sullivan and report author noted, “WatchGuard is an established competitor in the UTM and NGFW market. Their product strategy focuses on visibility, performance and integration of best-of-breed technologies that are simple to use and provide great value.”
Rodriguez highlights specific product and solution benefits that illustrate how WatchGuard achieved its leadership position. These include:
- WatchGuard Dimension’s ability to pinpoint security and performance issues streamlines management and usability.
- The flexibility of WatchGuard’s platform allows integration of only the desired security functionality for increased efficiency and ease of use.
- The consolidation of leading security technologies from best-of-breed providers onto the Fireware®platform delivers exceptional value to users.
- Tuning the platform for optimal use of commercial hardware, such as Intel processors, improves packet processing and enables increased performance and scalability of the platform.
- A roadmap with significant future improvements around Fireware® and other security technologies shows WatchGuard’s continued commitment to product development.
To learn more about how WatchGuard can help move you to the top of the network security food chain, click here.
How a Leading K-12 School Protects Student Data and Controls Web Access with UTM
Today we announced that a leading K-12 school in the Dominican Republic is using WatchGuard’s Unified Threat Management (UTM) solutions, and WatchGuard Dimension, to secure its network, keep student data safe, control web access, and more.
You can read the entire press release here, access the full-length case study here, or check out the mini case study graphic below.
In addition, if you missed the recent post titled, “5 Ways UTM Security Can Help Schools,” click here to learn more about bandwidth usage, reporting, wireless and more.
5 Ways UTM Security Can Help Schools
 Schools contain. Educators teach. Students learn. Simple, right? Well you’d think so, but as modernization occurs right in front of us, the methods of teaching are evolving. Students face new distractions in the form of always-connected devices, technology in their pockets, and social sharing applications that consume endless hours of time. But, these same tools that make today’s students the communication generation (thanks parents) are also the tools teachers are increasingly using to help educate.
Schools contain. Educators teach. Students learn. Simple, right? Well you’d think so, but as modernization occurs right in front of us, the methods of teaching are evolving. Students face new distractions in the form of always-connected devices, technology in their pockets, and social sharing applications that consume endless hours of time. But, these same tools that make today’s students the communication generation (thanks parents) are also the tools teachers are increasingly using to help educate.
This new influx of technology into schools has turned what used to be fairly simple networks, into advance networks that need to protect student data, manage access, and deliver performance for in-class technology applications. Security is a big part of this network ecosystem. And, as districts roll out new technology, security is moving beyond just protecting, allowing administrators to strategically manage access so students can get the information they need to be successful, while eliminating the distractions.
Gone are the days of the guy with the big key ring watching over the school grounds. Today, technology is a major component when working to keep kids productive and safe. In the security appliance world, Unified Threat Management (UTM) platforms hold the keys to success. Here are five things to consider when selecting a UTM solution and why they matter:
- Bandwidth Problems – Three to four devices per student can have a dramatic impact on bandwidth and create bottlenecks. With each student carrying a notebook, smart phone, and iPad, the UTM firewall is the first point of control for getting access to that bandwidth. If it can’t handle the amount of traffic, you have your first problem – bottlenecks. Increasing the size/bandwidth of your firewall will greatly help with the flow of data, bonus points for a multi-core design appliance working in parallel. Say goodbye to legacy firewalls.
- Operating Systems – Windows, Mac, Android, etc., a network security system must be OS agnostic, just like the real-world.
- Information Overload – Distractions are everywhere on a school campus, but in the virtual world, the problem is ten-fold. UTM solutions give schools the ability to limit online access with Access Controls, enabling students to access the sites and applications they need to learn (and what educators need to do their job and protect them from legal issues).
- Wireless Access – Today’s students expect wireless access at all times. Gone are the days of the telephone wire, the cable box, and RJ45 cable. Updating and improving the wireless infrastructure of a campus goes hand-in-hand with increasing the bandwidth of your firewall. Having seamless access point integration with your UTM can deliver student location recognition, help identify problem areas, and help you better plan out coverage.
- Dynamic Reporting – Real-time visibility is key to understanding what trends and problems might be happening on the network, and useful reporting options help keep teams informed and help shape new policy creation. A UTM solution should help you see, instantly, who your bandwidth hogs are, see where people are “going,” see which access points are the most heavily used and more. Make sure your solution can turn logs of data into security intelligence, so you don’t have to spend hours digging through information.
It’s clear that UTM solutions can help educators to better assist students in their learning career. Don’t take my word for it, check out the small excerpt below from a recent case study with the Walker School District in Georgia:

Because of the increase in classroom productivity due to WatchGuard’s innovative technology, students are learning more and performing better on exams.
“Since all the kids are staying on the ball with what they’re supposed to be doing in the classroom, our testing scores have gone up. We’ve had some of our highest testing scores this last year that we’ve ever had,” said Bob Swanson, Walker School District Network Administrator.
Test scores reports have been so attractive that Walker Schools has seen an increased number of student registrations from outside the district. Students who previously attended private schools have now switched to Walker Schools after seeing the innovative learning environment that has been created with the help of WatchGuard.
Check out the entire case study at http://www.watchguard.com/tips-resources/casestudies/watchguard-network-security-solution-provides-safe-environment-for-walker-schools.asp
Some additional education case studies include:
This post was written by Mark Romano, director of field marketing at WatchGuard Technologies.
The Difference Between UTM and NGFW
I got a call from a potential customer the other day while driving in the car with my family. After listening to the flood of TLAs (three letter acronyms) in the conversation, my daughter asked me what all that alphabet soup meant. Many customers wonder the same thing. What is DLP (data loss prevention) and why do you need it? Is IPS (intrusion prevention system) the same as APT (advanced persistent threat) and which one should you use? And so on. One of the biggest questions we hear is “what is NGFW (next generation firewall) and how is it different from UTM (unified threat management.) The real answer is that it isn’t as different as you might think. Let me explain.
UTM was born in SMB (small-to-midsized business.) It usually refers to a single box with multiple security technologies running on it (1). SMBs love it because it’s drop-dead simple to deploy and gives them every security feature they need in a single platform. NGFW is a subset of functionality, typically only 2 or 3 of the modules running on a single box. Yet, although it is less functional, many larger corporations tend to prefer to break up technology by location – they prefer to deliberately architect their security solutions to put the required security appliance close to the item it is protecting. E.g. the IPS belongs at the perimeter, but A/V and SPAM filtering belong next to the email server, etc.
Regardless of company size, and certainly regardless of which solution people choose, UTM or NGFW, WatchGuard is a very strong believer in unifying multiple scan engines onto a single box. It just makes sense. You needn’t pay for additional hardware, OS licenses, maintenance contracts, etc. In addition, it gives you the best chance of combatting today’s multi-vectored threats. Rather than keeping security tools in silos, with a different box / console / policy for each one, unify your security into the form factor that makes the most sense.
Perhaps the promise of lower operating costs combined with increased levels of security is what’s driving the growth in the integrated security market right now. Leading analyst firm IDC tracks the growth of the UTM market specifically at more than 13% this year. That’s the single highest growth rate in the network security market. When that many customers vote with their dollars, euros, pesos, and baht, WatchGuard notices and works even harder to give you the tools you need to succeed.
1. Gateway antivirus, SPAM blocking, URL filtering, Intrusion Prevention, Data Loss Prevention, Reputation Authority, etc.
V (5) Fundamentals of a Secure WLAN
Would you rather have something for free or pay for it?
Dumb question right? A free ticket to watch the Seahawks pummel I mean battle the Broncos in Super Bowl XLVIII beats paying $2,100 per ticket any day – unfortunately, not a choice you or I will likely have to grapple with anytime soon.
However, when it comes to wireless networking, this is a question we face all the time. Do I jump on the coffee shop’s complementary network after ordering my quadriginoctuple-frap, or do I use my provider’s network and eat into my data plan?
I would hazard to guess that most of us choose the free option – especially if we are going sit there and nurse that beverage all day – a choice that is repeated every day at coffee shops all around the world. In fact, we have gotten so used to making this choice as customers that we expect Wi-Fi access everywhere, including at work.
And, while an increasing demand for wireless networking may not be breaking news, many organizations still struggle when it comes to successfully deploying wireless networks in a secure manner.
So, in the spirit of the Super Bowl example above (nice work Hawks), I would like to present what coaches often call the fundamentals – only here I’ll talk about five fundamentals of securing your wireless network.
And, I’ll use roman numerals.
But no X’s or O’s.
I. Have a Plan
If you rush out, buy a couple of wireless access points and chuck them on your network, you’ll likely just make things worse. Instead, take time to understand your goals and consider some important pre-deployment questions such as:
- How many wireless users do I expect to have on my network?
- How much wireless coverage and what kind of bandwidth do I need?
- What kind of traffic do I want to allow/restrict? (Pay particular attention to social media and mobile applications.)
- How will I restrict access to the WLAN (by device, by user, by SSID, etc.)?
- Will both corporate and personal devices be allowed access to the WLAN?
It’s also a good idea to draft a network usage policy and have users sign it as this can help to encourage self-enforcement.
II. Implement Access Controls
Segmenting the WLAN (e.g. by VLAN), creating security policies for different SSIDs, enabling station separation, enforcing MAC control lists and user authentication can all help to ensure WLAN users, devices and traffic are only allowed to access intended resources.
III. Synchronize Wired and Wireless Networks
Make sure your wired and wireless security policies don’t conflict. If an access policy is being enforced on your wired network, ensure you are not circumventing it with your WLAN policy.
IV. Use Strong Passwords
Create strong WLAN access passwords and change them regularly. Some strong password creation tips can be found here.
V. Monitor, Adjust, Repeat
Regularly use monitoring tools and review traffic logs to see what’s happening on your network. This will help to ensure policies are being enforced as expected, identify new traffic types and applications to allow/restrict and recognize emerging threats.
To learn more about how WatchGuard can help you to deploy a robust and secure WLAN, check out our wireless page here.
5 Network Security Challenges Facing Schools and Campuses
Every industry has its unique set of network security challenges. In retail there’s dealing with credit card data and PCI compliance. In healthcare you need to deal with patient data and privacy requirements. Suffice it to say, the education sector has challenges that one might not initially consider and yet are very challenging in their own right.
Public school budgets are often strained today, forcing many IT managers to ‘do more with less’ and with growing security threats and booming IT innovation this is especially challenging. And while larger universities and campus-based schools may have larger budgets, they have larger challenges. Here are five network security challenges facing schools and campuses today:
1. Bring Your Own Device (BYOD) – The growing use of tablets and mobile devices by educators and students as they move to new ways of teaching and learning creates numerous network security challenges. BYOD device management is now a major need in districts and at campuses across the country. Just like any corporate organization, schools now need to think about network access policies, managing passwords more carefully, and understand how mobile devices are connecting to their networks.
2. Web 2.0 – Today’s students are more connected through social media than ever before and the Internet is playing an increasing role in education as teachers use it as part of their teaching arsenal. IT managers need to be able to allow access to certain sites and applications while restricting others. Finding this balance is not an easy challenge and requires new network security tools like Application Access Control.
3. Secure Remote Access – Student and teacher collaboration are playing an increasing role in education in today’s connected world. Today, students collaborate on projects and teachers provide feedback through cloud-based tools and by accessing school networks. IT managers need to be able to provide secure remote access to the tools that teachers and students are connecting to.
4. Multi-Point Access Solutions – Today, especially in campus environments, it’s not uncommon to have tens of buildings all connected to a single network. Being able to manage a distributed environment and its inherent security challenges needs to be simple and intuitive.
5. Identity Management – IT managers today need to be able to ensure that only authorized students and teachers can access computer and network resources. It’s through identity management that schools are able to effectively manage their acceptable usage policies and provide adequate control over access to applications.
There are many other challenges that education sector IT managers face, but these five are prevalent today and yet weren’t that long ago. Fortunately there are network security companies offering highly sophisticated unified threat management (UTM) tools and solutions, like WatchGuard. They’re flexible, powerful, robust, affordable, and can go a long way in easing the network security challenges facing schools and campuses. And, because the threat landscape is always changing, UTM solutions need to be designed to be able to easily add new network defense capabilities through security subscriptions, so costly hardware upgrades are not necessary.
IDC & WatchGuard Reveal Top 3 Security Challenges Facing Midsize Organizations: How Can UTM Help?
As 2013 comes to an end, Unified Threat Management (UTM) has grown up. What used to be an SMB security solution has now matured into a powerful platform for the midsize enterprise. The holy grail of defense-in-depth no longer requires costly point solutions, disparate management consoles, and hundreds of engineering hours to sift through log data. No, times have changed. Today, UTM is helping midsize enterprises overcome the complexity, performance and management challenges associated with protecting the corporate network.
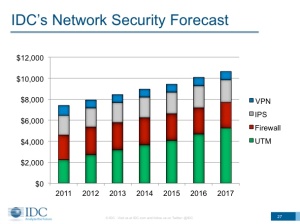
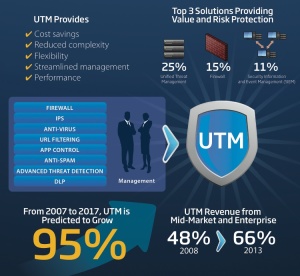
But, don’t take our word for it, the proof is in the data. According to IDC, from 2007 to 2017 UTM is predicted to grow 95 percent, and UTM revenue from mid-market and enterprise has grown 53 percent since 2008. Even more interesting, if you look below at the IDC graph from its most recent Network Security Forecast, it shows that UTM is the largest growing sub-function of the forecast (with the others having small or flat growth).
Below we’ll outline some of the challenges facing midsize enterprise, but you can also watch our recent IDC webinar with John Grady (research manager for security products and services) on this topic, or download our new IDC infographic, sponsored by WatchGuard Technologies, on UTM in the mid-market entitled “Protecting Your Midsize Enterprise with UTM.”
There are three key issues midsize organizations face today when it comes to network security:
1. Complexity – As the security perimeter has evolved, attack mechanisms have become increasingly sophisticated, and as solutions to solve these problems have multiplied, security professionals are overwhelmed with the complexities of securing the network. Mobile devices, virtualization, and cloud applications – all of these create architectural concerns for midsize enterprises. And, since these organizations traditionally have less staff and budget, the realities of integrating complex point security solutions to address these problems become more unrealistic.
2. Performance – The Internet continues to grow (IDC and EMC estimate in the IDC Digital Universe Study, sponsored by EMC in December 2012, an increase from 2.8 to 40 zettabytes from 2010-2020), as do shipments of mobile devices (19.8 percent by 2017). Organizations are using more applications, have unlimited sharing conduits, are using rich media, and are connected all the time – online activity has exploded. Roll in cloud applications and all of a sudden you have tremendous traffic coming in and out of your network. The gateway appliance can’t be the bottleneck. It must deliver higher throughput, better connection rates, be scalable, and offer layered security at the point of entry or exit (defense in depth).
3. Management – IT is supposed to do more with less. That’s the mandate. Innovate, while reducing operating costs. It’s a constant challenge. It’s why solutions need to do more for less. But, when it comes to network security…threats, regulations and complexity continue to increase, while IT security budgets lag – there’s a gap between organizations’ self-defense and the threats they face. To combat this issue, midsize organizations need security solutions that offer a single pane of glass for management, and solutions that simplify policy creation and integrate across multiple applications.
These three challenges are driving UTM adoption in the mid-market. By combining AV, IPS, firewall, application control, DLP and other security features, UTM can consolidate the visibility of threats, save the organization money, and can increase management and reporting efficiency. And, as threats continue to evolve, UTM will evolve with it, adding new security services and giving organizations the ability to easily visualize their security data (instead of simply reviewing log reports).
For more information on this topic, please view the webinar, download the infographic, or visit our UTM product page.
Graduating to Next-Generation Network Security Firewalls
Growth is exciting! Growth brings opportunities! Growth can also be somewhat scary when you’re goal is providing network security to three large, city campuses while also providing secure remote access to 40,000 students and over 1,500 staff.
That’s what Dave Newsham, the ITSS Service Delivery Manager at Leeds City College in the UK, was challenged with recently and we were delighted he turned to us at WatchGuard for assistance. With help from their IT partner, Epic Net the IT folks at Leeds decided to standardize on the WatchGuard Unified Threat Management (UTM) platform.
The first WatchGuard XTM 1520 replaced a Cisco firewall at the Technology Campus to deliver greater performance and control; while a second appliance has been installed at the brand new Printworks Campus, opened for the first wave of students this September. The third XTM 1520 will be installed in the Park Lane Campus this October to complete the secure multi-site network.
Our UTM firewall appliances provide safe IPSEC or SSL VPN authorized secure remote access to the College network and resources for all staff and students from multiple Apple, Windows, or Android platforms. As well as support for the full Microsoft Office suite of applications, every student has an Office 365 email account and associated online collaborative workspace.
In addition to providing full Layer 7 firewall protection and intrusion prevention, Leeds City College now has a central point of management, with the ability for policies to be easily deployed across the network, along with simplified administration and centralized logging and reporting.
With up to 14Gbs throughput, our XTM firewall appliances will be able to handle anticipated bandwidth growth over the next five years as well as the addition of increasingly complex rule sets, without loss of performance; while the clustered hardware configuration provides 100% resilience.
Dave sums up his experience in his own words:
The expansion of the College posed significant security challenges, but the WatchGuard solution has allowed us to efficiently and comprehensively implement network security for staff and students wherever they are on the network. The WatchGuard XTM firewalls are both affordable and uncomplicated to deploy and maintain, helping us ensure we meet compliance standards, and can easily scale to accommodate future growth. Deployment was pain-free, and we now have a more centrally managed, secure, and easy to administer multi-site solution and we are able to track, monitor, and review real-time access and reporting.
UTM Appliances and Securing 500 Banking Branches – What you Need to Consider
Achieving secure connectivity with failover, content-based Web filtering and centralized management of more than 500 locations is never an easy task for an IT team, but when it’s a financial institution with over 2,250 employees based globally it gets even more complex. This is what Adarsh Credit Co-Cooperative Society, a leading multi-state financial institution in India, was tasked with and they turned to our team here at WatchGuard for help.
Adarsh deployed our XTM 8 and 5 Series UTM appliances in its data centers, as well as XTM 2 Series UTM appliances at all of its branch locations. While banking accessibility was vital, the organization also needed to restrict Internet usage at branch sites. Setting up the right IT security policies and ensuring uniform administration across these sites was a key driver in the selection process, as it should be!
Adarsh’s AVP of IT, Ramlal Arya, summed up his challenge and spoke of his experience…
We implemented the Core Banking application and needed to connect all the branches with the central location so it could be accessed seamlessly. When employees and members access the Core application, speed is important, but the bigger challenge is ensuring all transactions are secure. Deploying WatchGuard helped achieve both goals. WatchGuard’s XTM also helps us achieve higher throughput, which results in faster application access across the board. Installation of the appliances in high-availability mode ensured uninterrupted connectivity and smooth failover from one appliance to the other. It proved fast and straightforward with the centralized policy management capabilities and has reduced our need for site-to-site travel. And, working with WatchGuard’s Expert Partner, TM Systems Pvt., made the entire process fluid.
WatchGuard has given us a secure platform that allows us to connect all locations seamlessly and gives members and employees secure connectivity quickly to the applications they need. On the IT side, it gives us more control and the ability to easily manage these appliances and policies from a centralized location.
UTM security can play a role in solving many complex challenges, from banking to PCI DSS compliance to distributed retail environments. Whenever evaluating a UTM appliance you need to consider five core traits:
- Quality of the features and capabilities – Here at WatchGuard, we use a best-in-class approach to delivering the smartest UTM appliances available; integrating the leading technology provider for each security layer – Websense for URL filtering, Commtouch for anti-spam, and so on.
- Security performance or UTM performance – Our UTM performance is up to 3 times faster than UTM performance from most of the other vendors.
- Manageability and ease of use – Something to also consider when evaluating the manageability of your UTM is whether there are premium charges for certain functionality that should be provided as standard options. Look for simple, easy-to-use management in your UTM appliance.
- Flexibility – UTM customers should be able to boost security services, subscriptions, and capabilities on the fly, without ever having to swap out hardware—further extending the life of the appliance. UTM appliances should also have a high degree of network systems interoperability. This way, regardless of the network topology mix (Cisco, Juniper or other), your UTM appliances will provide maximum interoperability.
- Reporting and visibility – Network visibility and security go hand-in-hand—and when it comes to achieving regulatory compliance (PCI DSS, HIPAA, CIPA, etc.), auditability is required. So, why would a security vendor not include visibility and reporting tools? Yet, many vendors charge extra for these capabilities, often requiring purchase of a separate product just for reporting.
These five traits were paramount to Adarsh and their requirements for the ultimate in network security management. Be sure they’re on your consideration check-list when you’re looking to secure your network!